In GCP, the highest level of permissions is typically associated with the "Project Owner" role. The Project Owner has full control over a project, including the ability to manage billing, modify project settings, create and manage other roles, and access and manage all resources within the project.
The organization administrator only operators at the hoc of the Root Node.
A Cloud Architect should be able to design a well secured architecture. Company XYZ seeks your expertise around enterprise-specific implementation. One of their major challenges at this point is the design workload architecture with the banking and insurance applications. Some of the questions you possibly ask;
- What strategies do you think we need to put in place to effectively handle security and privacy?
- How can we keep up with innovation while reducing cost.
- How do you seize opportunities while mitigating risk managing identities.
You need to focus on the solution that would manage workloads in a secured manner as well as inculcating the manager's suggestion that you should start off with the Identity and Access Management, that way, the team can have access to what you're building. The two applications will be;
a. Financial Application (Banking and investment) and Insurance Application (Individual & corporate). Technically you will have four projects and four leads.
TEAMS
Engineering Lead for financial Apps - Winston William
Engineering Manager for our E-commerce Apps-Ajibolou Gbacrown
The CTO of the company is - YOU
Chief Financial Officer - Vala Olaleye
Payment Profile Manager - Mbandi Micheal
Based on your professionalism you will develop an Architecture like this. This is for practice purpose.
STEP 1:
Login into your cloud admin console.
STEP 2:
Login into your console cloud account.
STEP 3:
Click on Identity & Organization.
STEP 4:
Click on begin the setup.
STEP 5:
A great feature about google cloud is that based on the above structure, you need to manage teams and workload in your environment by grouping the team according to their responsibilities. Google is suggesting that based on the previous years data it has gathered. In this case, you will have organizational admins that spare head teams. You also have the ability to create custom groups.
STEP 6:
Cloud admin console. You have the option to create custom groups. "create group". We don't have any set-up.
STEP 7:
Return to your google console. Click on create all groups and save and create. Should you get an error, refresh and you should create✅.
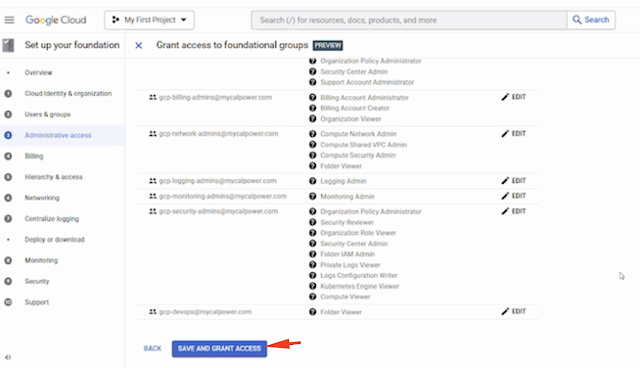
Within your google console, click administrative access and start. These are roles identified to be useful, google cloud is still "previewing", still testing to ensure its working. It automatically assign the role to individuals and you have to manually give permissions based on least privilege. At this level, this are group emails not administrator emails. Any policy that's given to the groups is applicable to individual in that group.
STEP 9:
Continue to billing. You need additional administrator assign to billing. Google cloud provided this to reduce risk. That's why you're giving all privileges.
STEP 10:
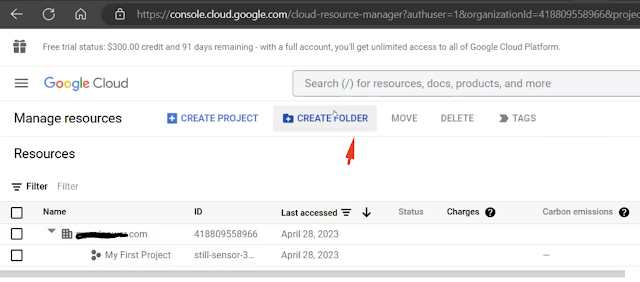
Search IAM and click "manage resources" and create folders and projects. Using the structure below to provision folders, projects and resources. Make sure the domain and location is specified.
STEP 11:
Create a project, choose the project name "banking project" and location "banking".
STEP 12:
Go to cloud storage, create a bucket inside the "banking project".
This is how you structure folders, projects and resources. Next slide, will guide on structuring Folders and projects. Enjoy your study steps!!😊
Referencing: Google documentation.















No comments:
Post a Comment